Features 1

CISO Reporting
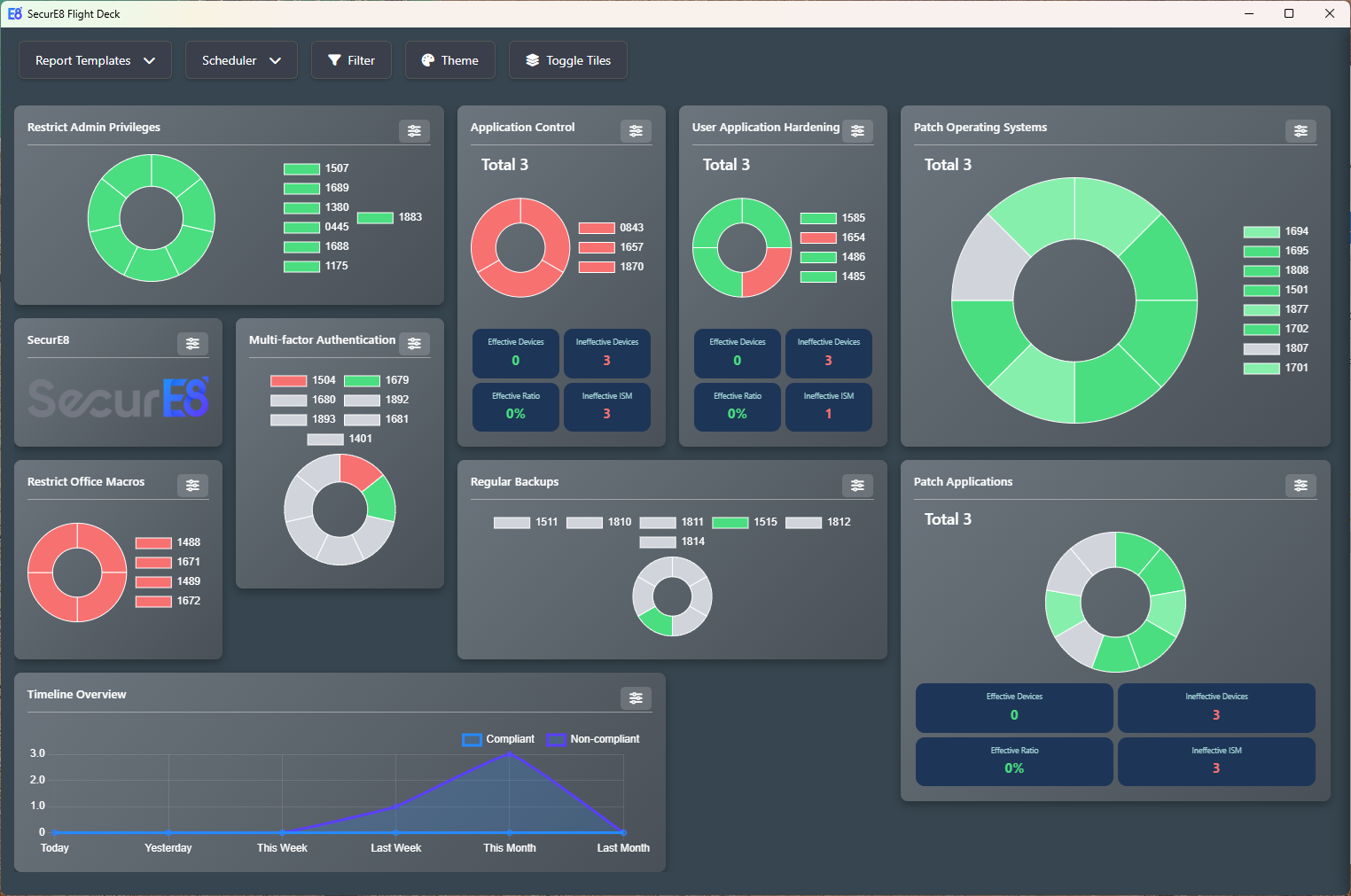
Dashboards on the Essential Eight Maturity Model provides an efficient, high-level view of your organisation's security posture. Meanwhile, detailed reporting with embedded artifacts streamlines audits, enhances accuracy, and simplifies compliance.
Real-Time Assurance
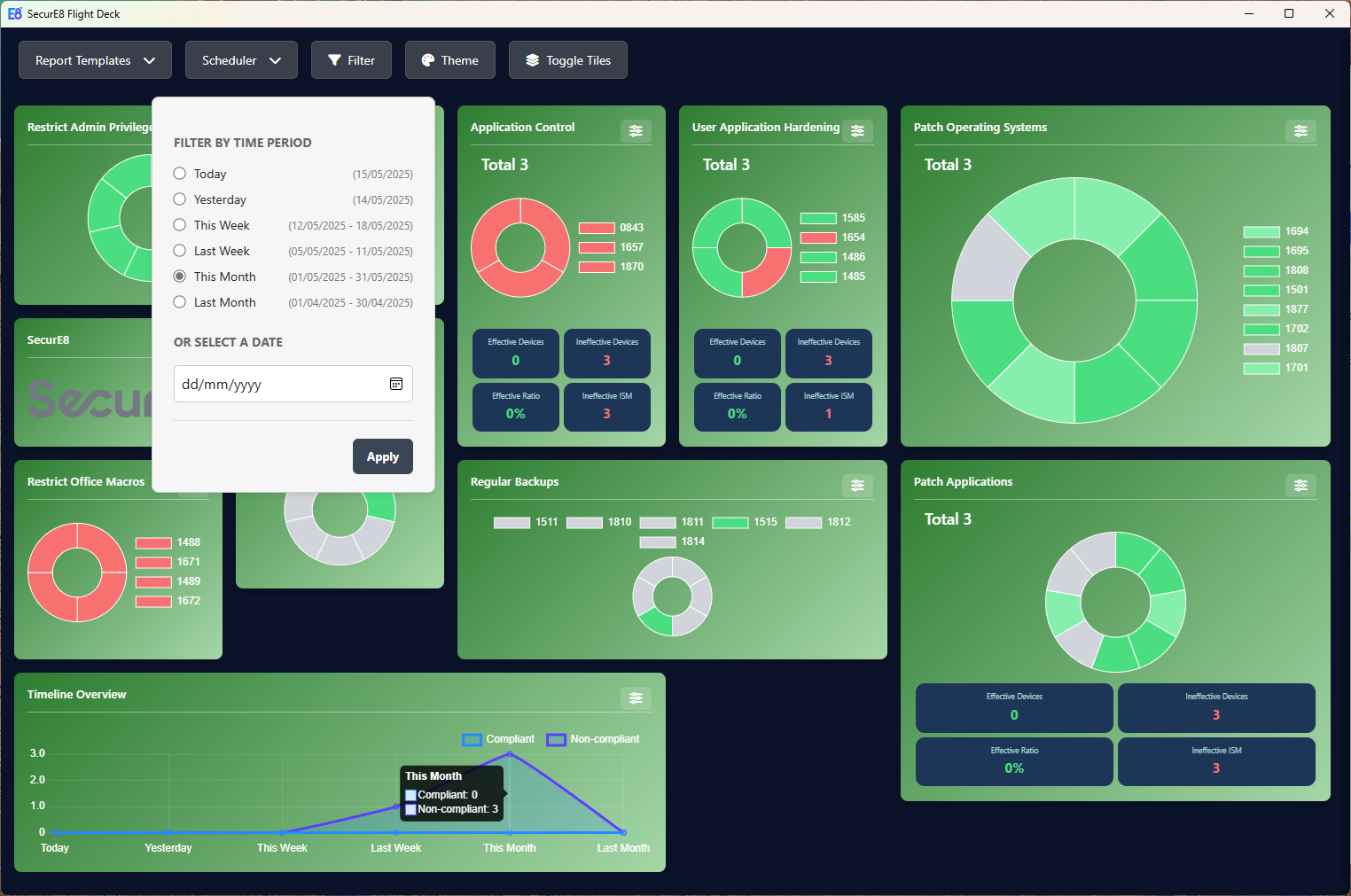
Continuous testing and monitoring of your Essential Eight security posture ensures a proactive and adaptive defense against evolving threats, keeping your organisation secure and compliant in a dynamic cybersecurity landscape.
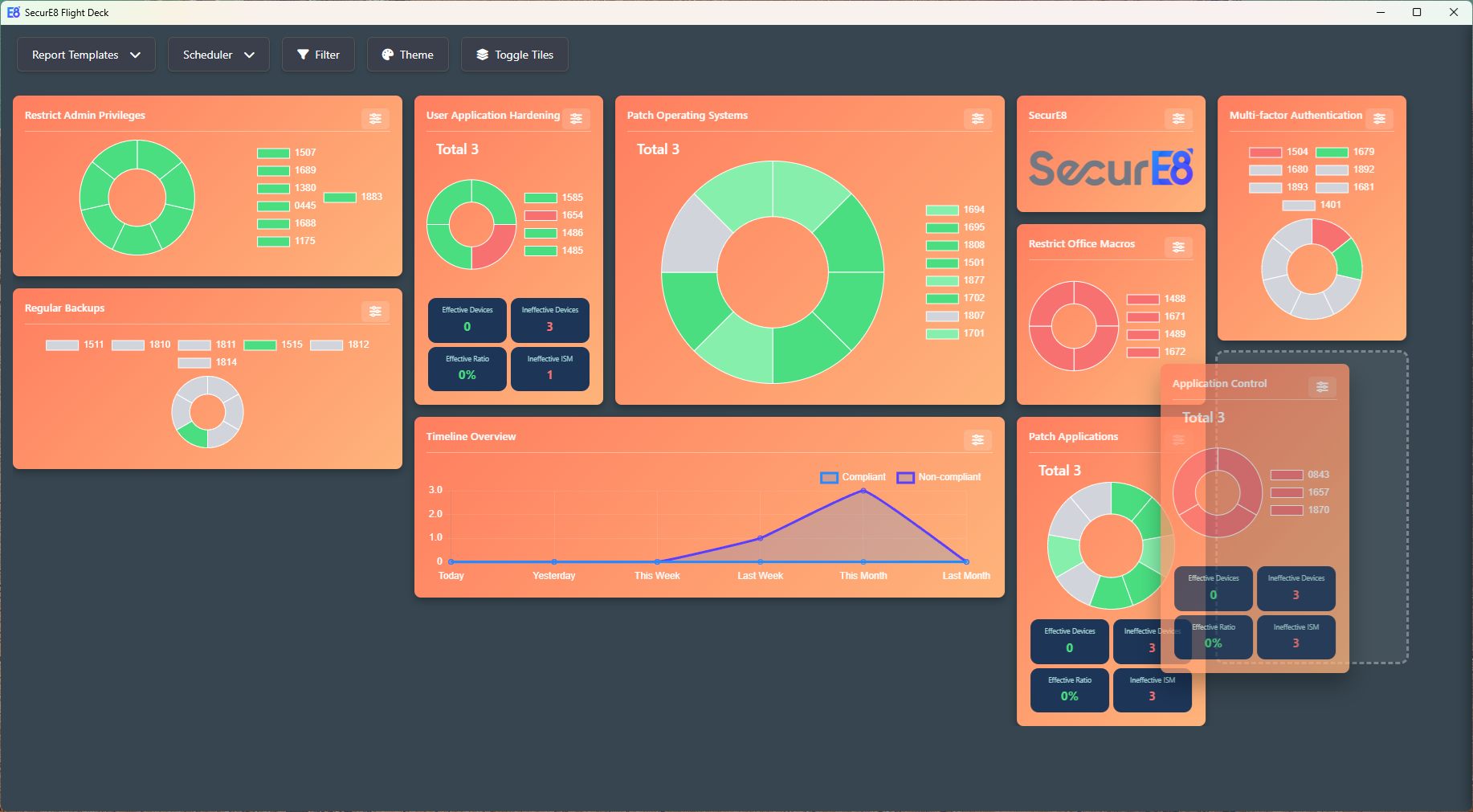
Holistic Viewpoint of Compliance
A high-level review of your organisation’s Essential Eight Maturity gives a clear view of security effectiveness, shows progress over time, and supports decision-making to maintain and improve cybersecurity resilience.
Device Specific Detail
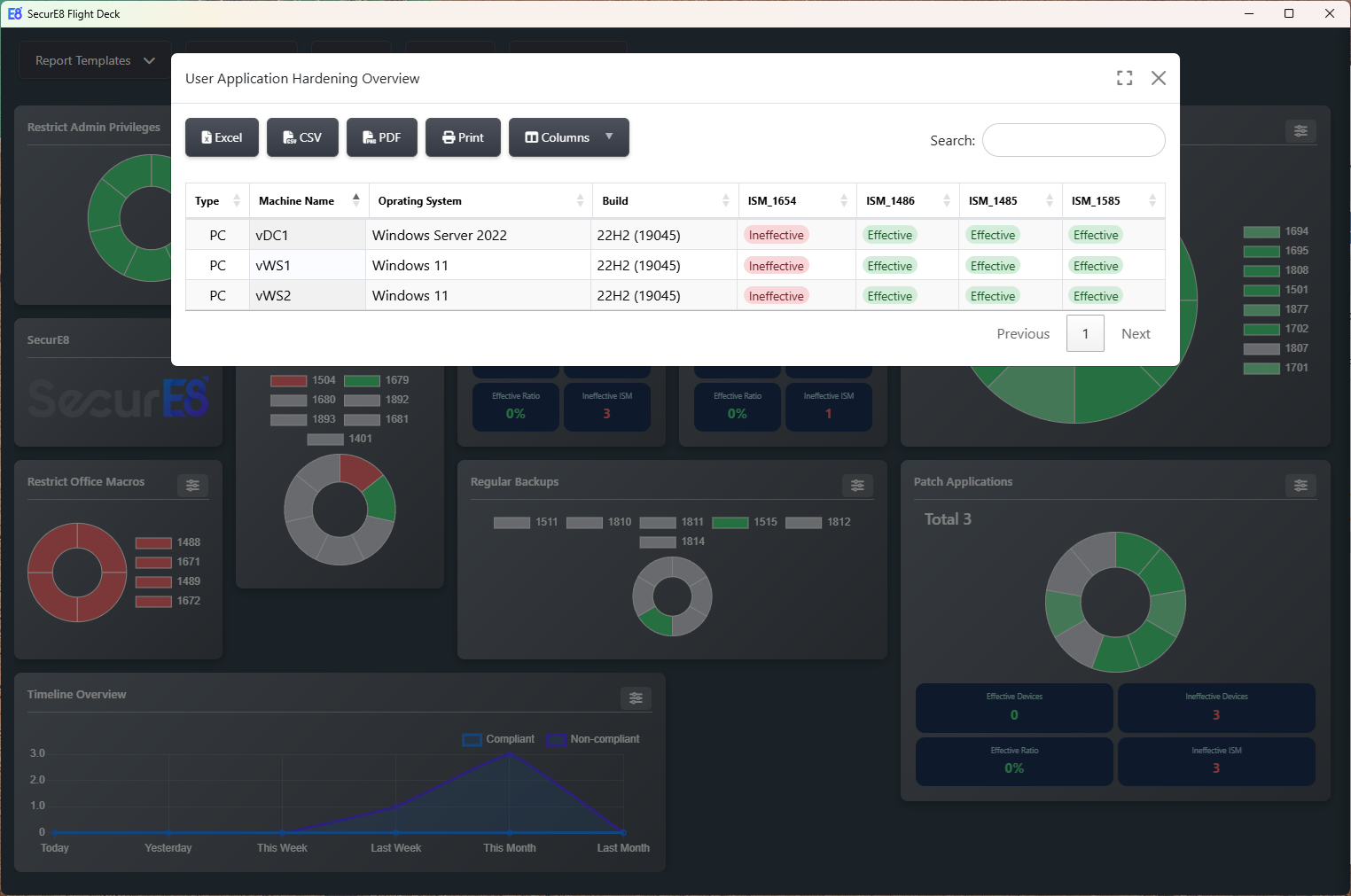
Granular device-level compliance information provides detailed visibility into the security posture of each machine, enabling auditors to investigate ISM control effectiveness, quickly identify issues, and ensure compliance through targeted corrective actions and efficient search capabilities.
Remediation Advice
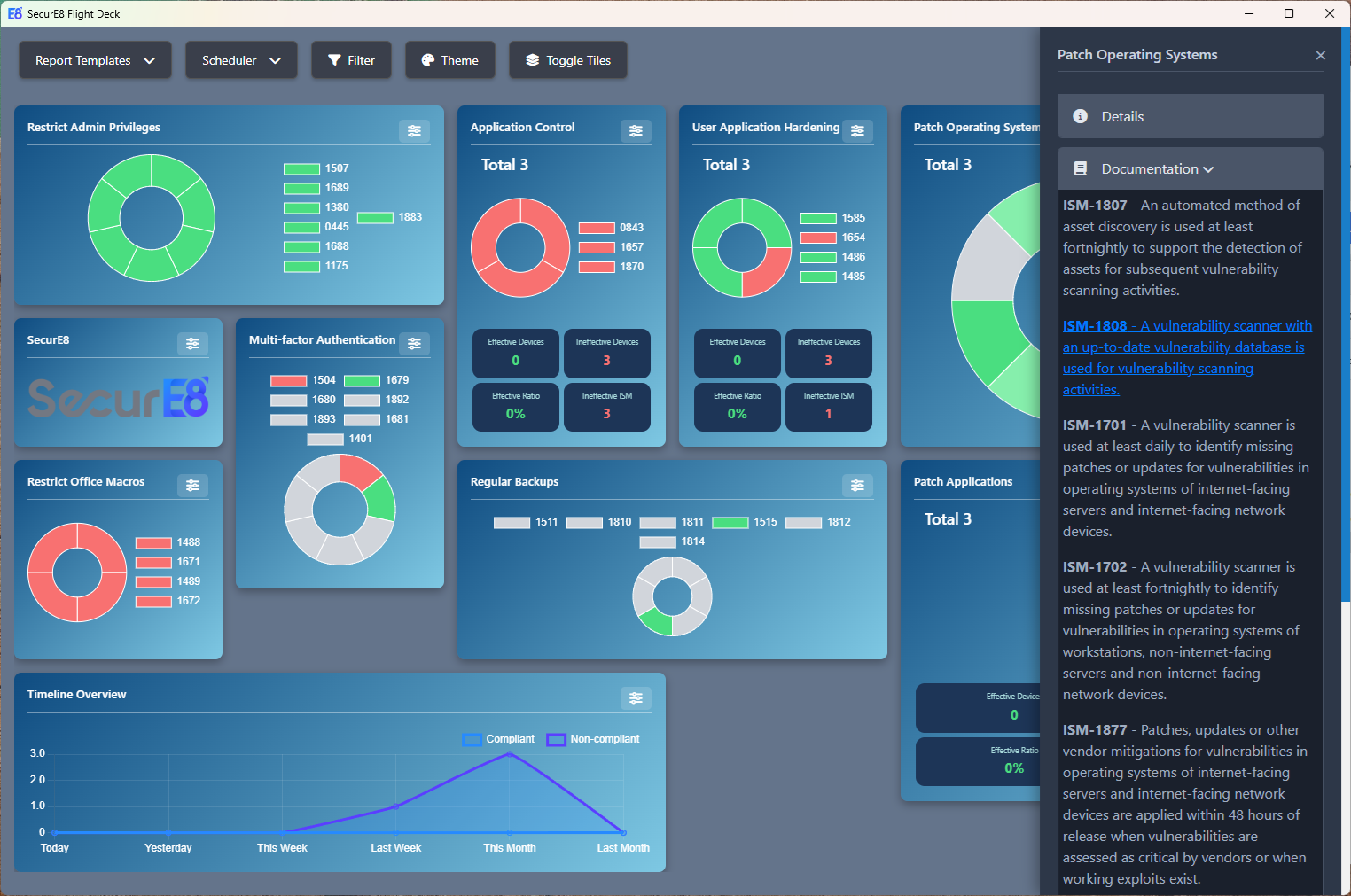
Operational and security uplifts are simplified by providing clear, actionable guidance to remediate Essential Eight compliance gaps, enabling even non-experts to perform audits effectively while streamlining communication and documentation for smoother implementation of security controls. No further need for the Essential Eight compliance guide.
Adaptable User Interface
With a high degree of flexibility, allowing users to tailor the interface and reporting experience to suit their operational needs. Tiles on the dashboard can be rearranged to prioritise the most relevant information for different roles or use cases. Organisations can customise logos and branding to align with their identity, and report templates can be modified to reflect preferred layouts or formats.